Gay dating apps still leaking location data
 Getty Images
Getty ImagesSome of the most popular gay dating apps, including Grindr, Romeo and Recon, have been exposing the exact location of their users.
In a demonstration for BBC News, cyber-security researchers were able to generate a map of users across London, revealing their precise locations.
This problem and the associated risks have been known about for years but some of the biggest apps have still not fixed the issue.
After the researchers shared their findings with the apps involved, Recon made changes - but Grindr and Romeo did not.
What is the problem?
Most of the popular gay dating and hook-up apps show who is nearby, based on smartphone location data.
Several also show how far away individual men are. And if that information is accurate, their precise location can be revealed using a process called trilateration.
Here's an example. Imagine a man shows up on a dating app as "200m away". You can draw a 200m (650ft) radius around your own location on a map and know he is somewhere on the edge of that circle.
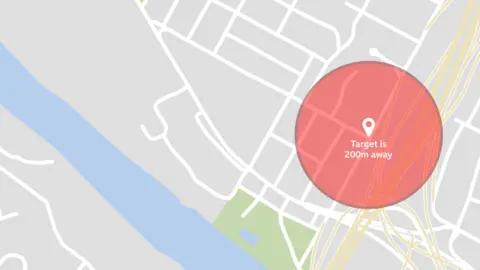
If you then move down the road and the same man shows up as 350m away, and you move again and he is 100m away, you can then draw all of these circles on the map at the same time and where they intersect will reveal exactly where the man is.
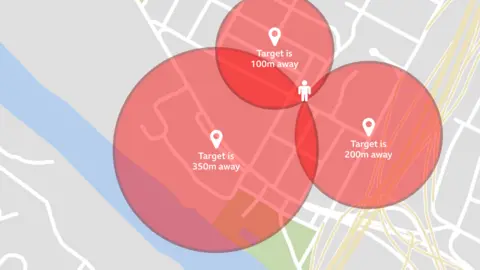
In reality, you don't even have to leave the house to do this.
Researchers from the cyber-security company Pen Test Partners created a tool that faked its location and did all the calculations automatically, in bulk.
They also found that Grindr, Recon and Romeo had not fully secured the application programming interface (API) powering their apps.
The researchers were able to generate maps of thousands of users at a time.
"We think it is absolutely unacceptable for app-makers to leak the precise location of their customers in this fashion. It leaves their users at risk from stalkers, exes, criminals and nation states," the researchers said in a blog post.
LGBT rights charity Stonewall told BBC News: "Protecting individual data and privacy is hugely important, especially for LGBT people worldwide who face discrimination, even persecution, if they are open about their identity."
Can the problem be fixed?
There are several ways apps could hide their users' precise locations without compromising their core functionality.
These include:
- only storing the first three decimal places of latitude and longitude data, which would let people find other users in their street or neighbourhood without revealing their exact location
- overlaying a grid across the world map and snapping each user to their nearest grid line, obscuring their exact location
How have the apps responded?
The security company told Grindr, Recon and Romeo about its findings.
Recon told BBC News it had since made changes to its apps to obscure the precise location of its users.
It said: "Historically we've found that our members appreciate having accurate information when looking for members nearby.
"In hindsight, we realise that the risk to our members' privacy associated with accurate distance calculations is too high and have therefore implemented the snap-to-grid method to protect the privacy of our members' location information."
Grindr told BBC News users had the option to "hide their distance information from their profiles".
It added Grindr did obfuscate location data "in countries where it is dangerous or illegal to be a member of the LGBTQ+ community". However, it is still possible to trilaterate users' exact locations in the UK.
Romeo told the BBC that it took security "extremely seriously".
Its website incorrectly claims it is "technically impossible" to stop attackers trilaterating users' positions. However, the app does let users fix their location to a point on the map if they wish to hide their exact location. This is not enabled by default.
The company also said premium members could switch on a "stealth mode" to appear offline, and users in 82 countries that criminalise homosexuality were offered Plus membership for free.
BBC News also contacted two other gay social apps, which offer location-based features but were not included in the security company's research.
Scruff told BBC News it used a location-scrambling algorithm. It is enabled by default in "80 regions around the world where same-sex acts are criminalised" and all other members can switch it on in the settings menu.
Hornet told BBC News it snapped its users to a grid rather than presenting their exact location. It also lets members hide their distance in the settings menu.
Are there other technical issues?
There is another way to work out a target's location, even if they have chosen to hide their distance in the settings menu.
Most of the popular gay dating apps show a grid of nearby men, with the closest appearing at the top left of the grid.
In 2016, researchers demonstrated it was possible to locate a target by surrounding him with several fake profiles and moving the fake profiles around the map.
"Each pair of fake users sandwiching the target reveals a narrow circular band in which the target can be located," Wired reported.
The only app to confirm it had taken steps to mitigate this attack was Hornet, which told BBC News it randomised the grid of nearby profiles.
"The risks are unthinkable," said Prof Angela Sasse, a cyber-security and privacy expert at UCL.
Location sharing should be "always something the user enables voluntarily after being reminded what the risks are," she added.
