The day a mysterious cyber-attack crippled Ukraine

 Getty Images
Getty ImagesThis time last week, an online attack brought chaos to Ukraine’s banks, hospitals and government, before spreading worldwide. The evidence suggests that money was not the aim – the real intention was disguised. Could it be a sign of something more serious to come?
On the morning of Tuesday, 27 June, Oleh Derevianko, the head of Kiev-based cybersecurity firm Information Systems Security Partners (ISSP), was at Bessarabska market, a popular food market in the heart of downtown. Derevianko was picking up a few things before heading out for the 300km drive to his parents’ village. Wednesday was constitution day in Ukraine, a national holiday, and he’d be using the mid-week break to spend a couple days with his kids. The kids usually spend two months of their summer holidays at their grandparents’ village home, so this was a rare chance for some summer fun together.
Alongside Derevianko, millions of Ukrainians, as well as businesses and government offices across the country would be off the clock tomorrow.
The day had begun with violence – at 8:15, a car-bomb killed a colonel in Ukraine’s military intelligence – but in this part of the world, executions are beginning to become a regular occurrence. It was, for Ukraine, an unremarkable day.
At around 11:00, Derevianko’s phone rang. It was a representative of a large telecommunications company that services Ukraine’s state-owned Oschadbank, one of the largest financial institutions of Ukraine and one of three ‘systemically important’ banks. It has 3,650 branches and 2,850 ATMs throughout the country. Although they were not an ISSP client, they needed help urgently: they were under attack.
“I passed the task to my team,” says Derevianko in an interview at the ISSP office during a scorching hot day in Kiev, “and I just continued on my way to the village. Attacks have been happening here all the time, so I wasn’t worried enough to change plans.”
 Getty Images
Getty ImagesDerevianko and the rest of the country had no idea about what was coming. A cyber-attack would ripple through the region, striking Ukraine’s banks, power grid, postal service, government ministries, media organisations, the main airport in Kiev, nationwide mobile providers and even the Chernobyl power plant. “By 13:00 or 14:00, it was 100% clear that we were under an ongoing and massive attack everywhere,” says Volodymyr Omelyan, Ukraine’s Minister of Infrastructure. It then spread worldwide – and the fallout is still being felt.
The most curious thing about the event? One week on, it is still not entirely clear why it happened, or who was behind it. So, how did the attack play out in Ukraine, and what is known about the motive?
The attack spreads
Around the time that Derevianko was passing the Oschadbank call onto his team, early signs of the attack were appearing elsewhere.
At 10:30, the first alert arrived at the situation centre of the National Security and Defence Council (NSDC), located just minutes from the banks of the Dniepr river. Thirty minutes later, a cybersecurity expert was rushing the news to the head of the NSDC, Oleksander Turchynov.
Turchynov – who served as Ukraine’s acting president after the ousting of former President Viktor Yanukovych – gave the command to run the response protocol approved by the National Coordination Center for Cybersecurity.
“In my cabinet, there is equipment allowing us to video conference with all the heads of security services of the country,” Turchynov tells BBC Future. Included in the video conference were the heads of the State Service for Special Communications and Information Protection, the Cyberpolice, the Security Service of Ukraine (SBU), and NSDC staff.
Meanwhile nearby, Roman Boyarchuk, the head of the Center for Cyber Protection had been instructing a special team, the Computer Emergency Response Team of Ukraine (Cert-UA), to figure out everything they could about the attack.
Within a few hours, Boyarchuk says, they understood the whole country was affected.
On the road
As Derevianko drove along to his parents’ village home, his phone rang again, and then again. As his staff relayed the details of the attack to him, Derevianko immediately realised that his vacation was over. Pulling over at the nearest roadside rest stop, he grabbed his laptop and sat down to work.
When Derevianko’s team began sending him the samples gathered from Oschadbank, what he saw disturbed him. “We immediately noticed some signs that this was not a ransomware attack,” he says.
 Getty Images
Getty ImagesRansomware is designed by criminals to infect systems and then demand a payment to unlock them. Think of the WannaCry attack that infected computers worldwide earlier this year – including the UK’s National Health Service.
“At first, I thought it was an APT (Advanced Persistent Threat) but soon I realised that we needed a new term to describe what was happening,” says Derevianko.
He only left the roadside stop in the evening to continue on to his parents’ home, albeit only for a few minutes. “I kissed my parents, my kids and headed to a hotel around 10km [six miles] from the village.” The hotel was the only place to get a working internet connection and so from there, Derevianko worked long into the night.
The next day, ISSP came up with the term “Massive Coordinated Cyber Invasion” to describe what they were seeing. They felt it was necessary to distinguish Tuesday’s chaos from the bevy of previous attacks against Ukraine in 2015 and 2016.
The reason it was so different, and even scary, says Derevianko, is that it seems a lot of what happened during the attack was automated, intended to deceive and distract its victims, and thereby disrupt the response.
Lesley Carhart, a security researcher with nearly a decade specialising in digital forensics and incident response, adds that the strategy far outweighed the technical sophistication of the attack.
“Every method of exploitation that the attack used to spread was preventable by well-documented means,” Carhart tells BBC Future. “What was devastatingly brilliant was the strategy behind the attackers' application and targeting.”
 Rob Engelaar/AFP/Getty Images
Rob Engelaar/AFP/Getty ImagesIt was able to intercept passwords, to capture administrative privileges, to delete logs, to encrypt, to wipe and perhaps most importantly, believes Derevianko, it was able to recognise specific “hashes” on machines and networks and seemingly leave them alone. In short, it was more surgical than typical malware in what it attacked, he claims.
The last part troubles Derevianko the most.
“The initial organisations that were hit, even in the networks where we saw most of the computers wiped out… there would be some machines that survived,” he says. “This immunity is strange. How did they survive, but more importantly, why?” At the moment, it’s not clear.
From ransomware to nation state attack?
As Ukrainians coped with the initial chaos, cybersecurity experts in Europe and then America slowly began to realise that the attack was outside the norm – and could reach beyond Ukraine’s borders.
One of those was The Grugq, a well-regarded veteran information security researcher, who uses a pseudonym. “I saw someone retweet the Ukrainian Vice Prime Minister’s photo of his computer screen,” The Grugq tells BBC Future. “After that went by I saw a tweet elsewhere about the car bomb assassination. And that got me somewhat on the ‘things are happening in Ukraine’ track.”
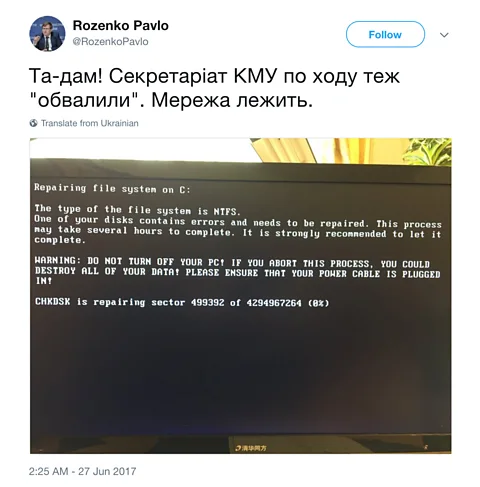
Ukraine's Vice Prime Minister tweeted a government screen during the attack (Credit: Rozenko Pavlo/Twitter)
In Toronto, Kevin Magee, global security strategist at Gigamon, got his first alert as he was stepping out the door to get to work. By 10:30 EST, during a meeting with security colleagues in the city’s financial district, Magee says one of the men checked his phone and looked up rather annoyed, saying, “yep… another Petya alert”.
Ransomware malware going by the name of Petya has been known to exist since 2016. This wasn’t Petya though – it was a modified, souped-up version.
 Getty Images
Getty ImagesNone of Magee’s colleagues were taking it seriously yet at that point, he tells BBC Future. “It wasn’t yet getting much attention from anyone," he says. “That was likely just due to simple alert fatigue that most security professionals are beginning to suffer from.”
But 30 minutes later, their phones started exploding. The people in the room began stepping out to take the calls but they didn’t seem to be coming back.
“One after another, they just started to melt away and disappear and it became obvious that something was up,” says Magee. “I snuck a look at my own phone under the table and my inbox was already full of questions as well as updates and Twitter was completely lit up too. [It] was obviously becoming a bit of a big deal.”
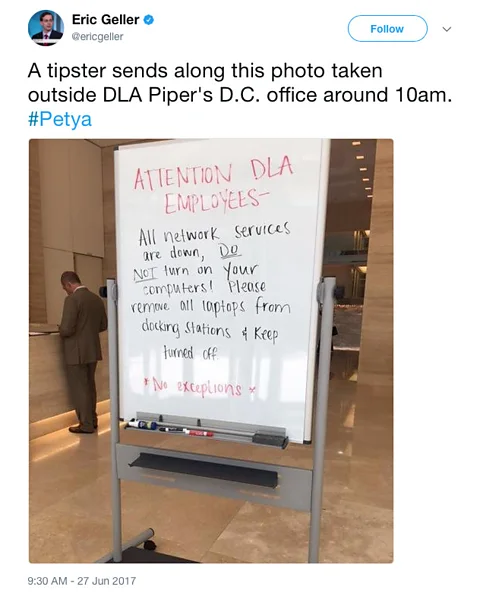
At that point, the attack targeting Ukraine had made its way across the Atlantic, to the Washington DC office of DLA Piper. A whiteboard at the office’s entrance read “DO NOT turn on your computers” (below). Seeing that message indicated to Magee that this attack was on a different level.
Also in Washington DC was Beau Woods of the the Atlantic Council’s Cyber Statecraft Initiative, in the Brent Scowcroft Center on International Security. BBC Future spoke to Woods, and Jonathan Nichols, a former US military IT expert, as the attack was unfolding.
“By the end of the day, we’ll know a lot more,” Woods told BBC Future at that time, “but I could see multiple scenarios. It could be the group that spread Petya, or it could be someone else modifying what they used. And it could be that Ukraine was ground zero and it spread from there, or it maybe that Ukraine was just the first place it hit and gained publicity.”
The next day, the picture was becoming clearer for them both. “There's still a lot to wait for before I feel good about attribution,” said Nichols on 28 June, “but I'm fairly confident the combination of crappy ransomware with government mandated software suggests that the purpose wasn't financial.”
Woods agreed. “I'm less convinced that this is actual ransomware, it looks disguised as clumsy ransomware,” he said.
Later that day, Russia-based Kaspersky Labs and well known cybersecurity expert Matt Suiche both concluded in heavily circulated blog posts that the appearance of ransomware was a disguise, verifying what Derevianko from ISSP had told BBC Future the day before.
“Our analysis indicates the main purpose of the attack was not financial gain but widespread destruction,” a Kaspersky spokesperson said. In other words, the aim was to create chaos, attacking Ukranian digital infrastructure, making it harder for businesses to operate and crippling government services.
 Getty Images
Getty ImagesIn a webinar, Juan Andres Guerrero-Saade, from Kaspersky’s global research & analysis team, and Matt Suiche, from Comae Technologies, said that they have labelled the attack as destruction instead of ransomware.
“Normally that wouldn't be the consideration with something considered ransomware, because with ransomware, you are blocking access to files for financial motives, and while this appeared to be ransomware, we think it fits better into the category of destruction.”
Suiche later messaged BBC Future adding that the attack was ‘entirely’ targeted against Ukraine.
As details and confirmations emerged, Woods messaged BBC Future to ask: “If money wasn’t the motive, then what was?”
Continuing impact
On 28 June, the fallout of the attack became clearer.
Maersk, a global shipping giant, confirmed on Twitter that they had been hit by the attack rendering many services "not operationally effective". Maersk, along with several other multinational corporations affected by the attack, declined a request for interview.
Oschadbank – the state-owned bank who had first alerted Derevianko – closed its 3,000+ physical branches for days, but their online banking is functional.
Andrey Begunov, the Chief Information Officer of PUMB, a large financial institution owned by Ukrainian billionaire Rinat Akhmetov, says that in his 23 years within the banking and IT sectors of Ukraine, this was the worst situation he’s ever seen. His bank wasn’t even hit, but the chaos he saw amongst competing banks who had been hit was enough to shock him.
Even as far as the US, a health network with 3,500 employees spread across two hospitals, 60 doctors’ offices and 18 community facilities was brought down by the attack. The downtime forced patients to delay procedures.
 Getty Images
Getty ImagesIn Ukraine, the country’s Minister of Health, Ulana Suprun, told BBC Future that her office was taken back in time about 30 years. “We’re working by pen and paper again,” she says. “There are so many things we can’t do because we’re down,” says Suprun.
For example, her ministry centralises the distribution of medicine across the vast territory of Ukraine’s 24 regions. When hospitals in those regions run low on medications for patients, they contact the ministry to source medicine. Either the ministry has them, or they locate them in other regions and send them to the region in need.
“But we can’t relay those messages right now, except for by phone, so imagine how crippling that is to us,” says an exasperated Suprun. “What used to require one email, copied to the 24 regions now requires 24 separate phone calls before we can find the drugs. Ukrainians can’t get medical documents because our internal system is down. I can’t pull up statistics for a meeting I have this week about Aids. I couldn’t even tell you which hospitals went down because they can’t reach us.”
Derevianko from ISSP knows of at least one hospital went down during the attack. It was the one in which he was scheduled to have a minor surgery last week. He tells BBC Future that the computers were down when he arrived for intake, so the hospital was back to pen and paper.
Murky motives
In over 25 interviews BBC Future conducted during the week after the attack, cybersecurity experts seemed to come to a consensus about two things. First, this attack was not about the money, and secondly, it was targeted against Ukraine.
And these two conclusions produced a bevy of other questions within the community.
For starters, does the seemingly intentionally destructive nature of the attack constitute the use of a cyberweapon? For some, like Magee, it very obviously did. “I don’t think you can call it anything else. I think it’s the equivalent of a test, and I think someone is building and testing an arsenal, wrapping them as ransomware, and distracting people from what’s really going on.”
Others were far less sure. “If you’re a nation state and you want to target your enemies, why send warning shots and be very noisy about it?”, asks Brian Honan, an independent information security consultant based in Ireland. “That doesn’t seem sensible. If you wanted to cause damage, you'd do it quietly, in a stealthy way until you need to pull the trigger.”
But Nicholas Weaver, a longtime cybersecurity veteran specialising in worms (malware that autonomously replicates itself to spread to other computers) believes it was devastating as a weapon. “You're launching your attack against anyone who does business in Ukraine,” says Weaver, “If your goal is to damage Ukrainian business relationships and business interests, I’m hard pressed to think of a better worm. This is significant damage in one sweep.”
 Sergei Supinsky/AFP/Getty Images
Sergei Supinsky/AFP/Getty ImagesSo could the motive have been political, and therefore, was it created, sponsored or organised at the level of a nation state?
On 2 July, BBC News reported on a statement by Ukraine’s security service, who claimed to find proof that Russia was behind it. Moscow denied any involvement, calling the allegations “unfounded”.
New warfare questions
If a nation state was involved, and it was a cyberweapon, we may be entering new territory in geopolitics. Where does it fit into conventional notions of warfare and espionage? Is it an act of war? And if it was an act of war that denied healthcare and services to civilians, does that constitute a war crime?
“These are questions we need to ask,” says Beau Woods. “Soldiers don’t shoot at the Red Cross on the battlefield because it’s a one-way ticket to the Hague, and civilian healthcare is one of the most off-limits things we have. I’m not a lawyer, but it seems there’s been a very legal line that’s been crossed. For decades and centuries we’ve treated healthcare as a moral right… Hospitals are sacrosanct. It must trigger a reaction.”
Regarding the question of attribution to a nation state actor, cybersecurity experts interviewed by BBC Future believed the size of the group required to conduct such an attack would be between 10-20 individuals. Some believed it could be as few as two or three developers, but at least several more individuals would be required to set up and test the attack, and the months they would need would necessitate some sort of HR team as well.
“To actually carry out the full operation,” says Robert M Lee of cybersecurity firm Dragos, “you’ve got management, back office support, healthcare, financials. You’re talking a team of 10 people. But just the malware design and execution, up to five.”
Although attribution to any single actor is too early, the notion that it was cyber criminals seems to be teetering. If the attack was not financially motivated, then what could motivate, and who could resource a startup-sized contingent of actors to pull off such an attack.
“I'm not allergic to the idea that this is nation state anymore,” Sean Sullivan of cyber security firm F-Secure tells BBC Future. “There are compelling details to continue analysing this as a nation state attack. I don't think this theory is garbage.”
For Derevianko, this attack is just the inevitable continuation of something he warned senior Ukrainian officials about three years ago.
“In 2014, I talked to so many people in high levels of government saying that we need to start preparing professionals capable of reacting to really advanced cyber-attacks,” he says. “I told them, if we don’t start preparing now, we’ll be overwhelmed with attacks in three years.”
If Derevianko is right, then, there could be more days like 27 June to come for Ukraine – and if so, the fall-out from these unpredictable infections will spread out into the rest of the world too.
If you liked this story, sign up for the weekly bbc.com features newsletter, called “If You Only Read 6 Things This Week”. A handpicked selection of stories from BBC Future, Earth, Culture, Capital, and Travel, delivered to your inbox every Friday.
